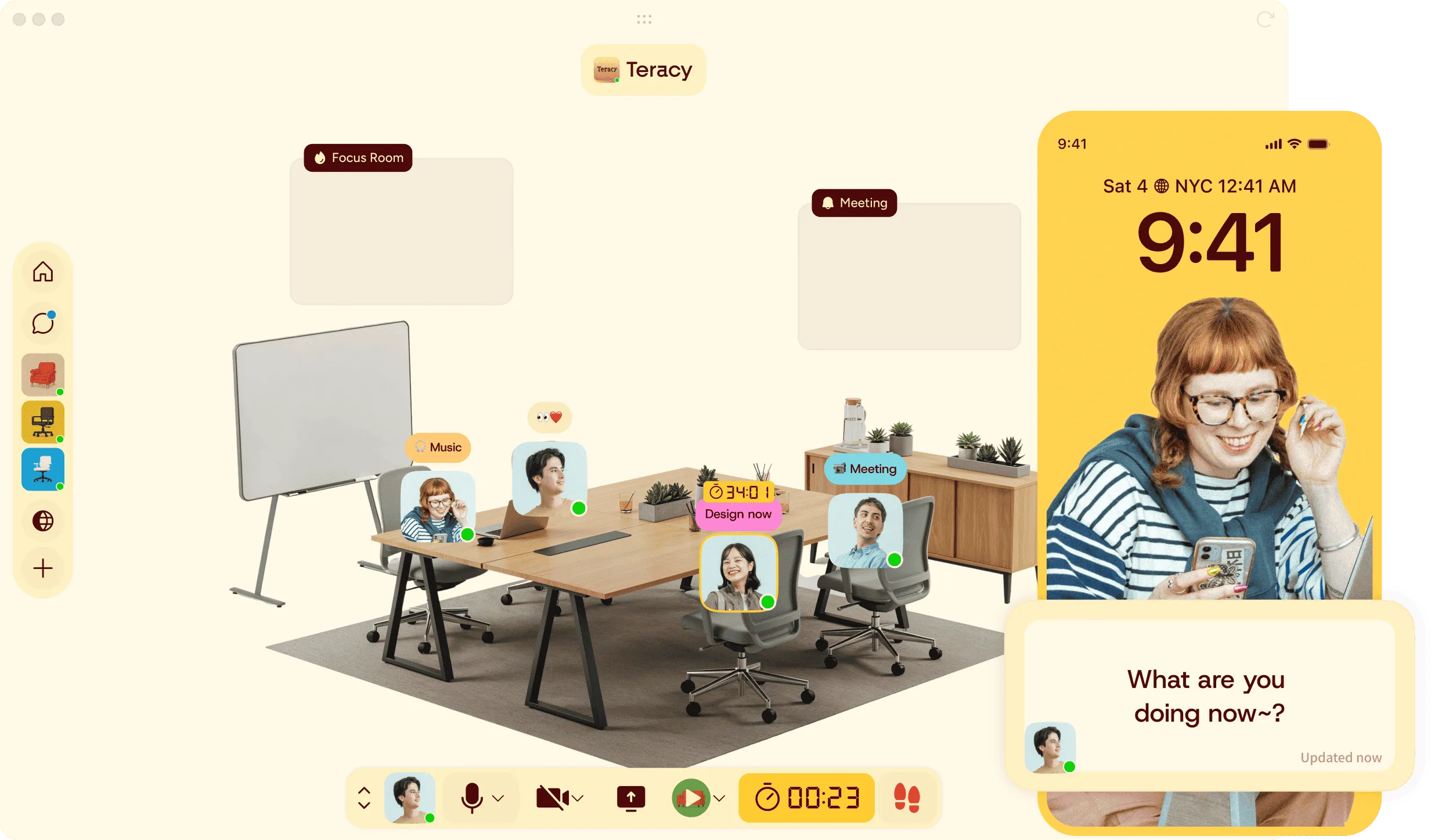
At Teracy, our mission is to create a world where location or loneliness never limits human potential. For everyone to thrive, safety and peace of mind come first.
We take the security of your data in our coworking app Teracy very seriously.
Our goal is to make our security practices as clear and transparent as possible, so that you can feel confident in your online space with Teracy.
If you have any questions about security, please contact from Contact. We’ll do our best to respond as quickly as possible.
Infrastructure
Teracy is hosted on Google Cloud infrastructure.
Customer data is processed and stored in data centers located in Japan and the United States, all of which comply with Google Cloud’s strict security and compliance standards.
Data Protection
Access Logs
All access to customer data is logged and auditable.
Encryption
Data is encrypted in transit using TLS 1.2+ and at rest using AES-256 or equivalent methods.
Data Deletion
When a space is deleted, all related data is promptly removed. Any associated backups are fully purged within 7 days.
Authentication & Authorization
Customer accounts are protected using Google Cloud’s authentication platform.
Internal systems follow attribute-based access control (ABAC) and the principle of least privilege to ensure secure access to customer data.
Vulnerability Management
Teracy services run on containers, with base images automatically updated by Google Cloud to ensure timely patching and security.
Call Security
Call Infrastructure
Voice and video calls are powered by LiveKit Cloud. For details, see https://livekit.io/legal/security .
Call Data Storage
Teracy does not store any call content (voice, video, or screen sharing).
Call Participation
Joining a call is protected by both Teracy authentication and LiveKit authentication.
Encryption
All call data is encrypted in transit using LiveKit’s security protocols.
Internal Controls & Confidentiality
Employee access to customer data is strictly limited to what is required for work.
All access is logged and subject to audit.
Every employee is bound by confidentiality agreements prohibiting any unauthorized use of customer data.
Compliance
Teracy’s operations are informed by international standards such as ISO 27001.
We are committed to continuously strengthening our security measures in line with relevant laws, regulations, and industry best practices.